 The picture above is my primary photo on my friendster, because there is someone who asks me how to create images like that, so I decided to make it a tutorial on my blog.But I did not write it to this day because it's too much, so I created a tutorial in the form of documents that can be downloaded by anyone, because I indonesian people so I make this tutorial with indonesian language so that anyone can understand and can practice it.
The picture above is my primary photo on my friendster, because there is someone who asks me how to create images like that, so I decided to make it a tutorial on my blog.But I did not write it to this day because it's too much, so I created a tutorial in the form of documents that can be downloaded by anyone, because I indonesian people so I make this tutorial with indonesian language so that anyone can understand and can practice it. Manipulation images with the fire effects
 The picture above is my primary photo on my friendster, because there is someone who asks me how to create images like that, so I decided to make it a tutorial on my blog.But I did not write it to this day because it's too much, so I created a tutorial in the form of documents that can be downloaded by anyone, because I indonesian people so I make this tutorial with indonesian language so that anyone can understand and can practice it.
The picture above is my primary photo on my friendster, because there is someone who asks me how to create images like that, so I decided to make it a tutorial on my blog.But I did not write it to this day because it's too much, so I created a tutorial in the form of documents that can be downloaded by anyone, because I indonesian people so I make this tutorial with indonesian language so that anyone can understand and can practice it. Hidden Name the computer list in the browser and the My Network Places
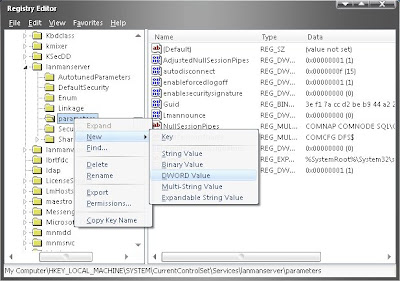

4. Enter the value 1 on the value of data

5.Restart computer and see its changes.
Changing the name of My Computer, My Documents, and Recycle Bin on the desktop Computer.
If you want to change the name of a folder so we live right clicking the folder and select rename, but if I change the name of My Computer, My Documents, and Recycle Bin? Certainly can not be done in the same way, you must modify the value in the registry editor to change the its name.
Here is a desktop icon that value must be changed:
 2.At Run box, type regedit and click Ok.
2.At Run box, type regedit and click Ok.
 3. Open the HKEY_CURRENT_USER folder.
3. Open the HKEY_CURRENT_USER folder.
 4. then open the folder Software \ Microsoft \ Windows \ CurrentVersion \ Explorer \ CLSID.
4. then open the folder Software \ Microsoft \ Windows \ CurrentVersion \ Explorer \ CLSID.

 5. select the folder (20D04FE0-3AEA-1069-A2D8-08002B30309D) (My Computer code value), then double-click Default.
5. select the folder (20D04FE0-3AEA-1069-A2D8-08002B30309D) (My Computer code value), then double-click Default.
 6. In the Value data, type the name of anything, this will change the name of My Computer, for example I just typed "Komputer ku" and click Ok.
6. In the Value data, type the name of anything, this will change the name of My Computer, for example I just typed "Komputer ku" and click Ok.
 7. close the Registry Editor window, and then refresh your desktop to see the results.
7. close the Registry Editor window, and then refresh your desktop to see the results.
Speed up Windows XP
All computer users want certain bias computer belonging to its work more quickly, the following are a few tips for the computer user's computer that it is a bit slow, this may not be able to make a computer faster but this could help a little. To speed up the performance of Windows XP, you just remove the service usually is not needed in the yag-Load by windows XP. 1.Buka control panel with the click start and select control panel.
 2.Open Administrative Tools, then double-click on the Service.
2.Open Administrative Tools, then double-click on the Service.

3.Then you switch the non service following. Alerter, Clipbook, Computer Browser, Fast User Switching, Human Interface Access Devices, Indexing Service, Messenger, Net logon, Netmeeting Remote Desktop Sharing, Remote desktop Help Session Manager, Remote Procedure Call Locator, Remote Registry, Rounting & Remote Access, Server, SSDP Discovery Service TCP / IP NetBIOS Helper, Telnet, Uniersal Plug and Play Device Host, Upload Manager, Windows Time, Wireless Zero Configuration (for wireless networks) Workstation.
How:
-select service that would disable.
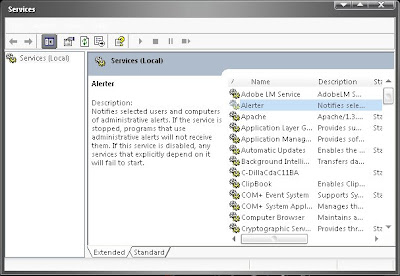 -Double click until the window will appear like this.
-Double click until the window will appear like this. -In the Startup-type you select Disable, and then click OK
-In the Startup-type you select Disable, and then click OK
 After all the necessary service that is not closed, Reboot computer or restart computer to see the results.
After all the necessary service that is not closed, Reboot computer or restart computer to see the results.
Nanobots
In addition to up intelligences, robots aka tiny nanobots also make people remember things better. In fact, people could soon enter the environment through a virtual reality system sarafnya automatically.
Kurzweil and his team are very confident that combining machine and human - with embed it in the body - will be able to push up levels of health and intellect far above the standard at this time. In fact, human life? half? robot that will be part of social life itself. ? We? he said,? Using technology to improve physical and mental together.
Toh, Kurzweil rush assert that it will not become a kind of alien invasion of intelligent machines that threaten the human existence and menggusur. Engine, he said, just realizing beratus-hundred things that people want to do, both at the limit or more, and intellect in various areas of life.
Not only created the engine for injected in the body, the researchers also revealed that the success in setting up the hardware and software with the intellect, such as imitation of the human being, including emotional flexibility and ingenuity. ? We have to be ready with the human community engine,? he said.
Just enough information, Kurzweil is one of 18 influential thinkers 21st century who have chosen to identify the various challenges associated with the human race. Other figures are the founders of Google, Larry Page, and genetics expert, Dr. Craig Venter.
One of the success of the project reject the measure of trust that is growing exponentially from a data processing capability. In addition, at the same time the size of the various device technologies shrink. The two things that trigger the development of computer mikroskopik.
The experts also said that technology, is a to bring an to make an accurate prediction of growth and changes in the computing world's attention with what has been achieved successfully in the field of development of the computer during the last 50 years. Base on it, they be convinced to 25 years in front of computer will be increased to billions of times. Meanwhile, the size of a smart machine that will shrink to 100 thousand times.
Today, he said, people can put the computer seukuran bean seeds in humans to treat Parkinson disease. Neuron damaged by the disease can also be replaced by these sophisticated devices.
As known, some time ago a number of scientists from the Massachusetts Institute of Technology successfully cure a number of hamster is blind. The story, the researchers in the laboratory of brain damage the animal does it related to the function of vision. Animal that is injured then injected with synthetic peptides of nanometer-sized five.
Material is later able to unify the brain cells that cause damage without scar scar. Things that make the animal is blind can see again. Interestingly, the trial was also successful in the older age of the animal that is suspected selnya regeneration ability is not working optimally. ? This makes us very surprised and happy,? said Dr. Rutledge Ellis-Behnke, a specialist from MIT neuroscientist.
Similar to that conducted by researchers from MIT, Kurzweil and colleagues also optimize the nano technology. The result, they are ready to bear the computer that has a size similar to a blood cell. Data processing engine that can be injected and creep in the human body. If lodged in the brain, then he will redouble level intellect.
Bermuda Triangle

What is called the devil hole? That's because the books that I read when it ships, boats, and aircraft or the like passing through the triangle that the ships, boats, and planes will fall and sink to the triangle and it disappeared. there are some who think that the Bermuda Triangle is the palace of the jinn and the Dajjal, they live like men in the water but we can not see them, aircraft and ships fell as rapt by the Dajjal and the jinn to be a slave for them, da says they are very smart, they kidnap people-smart people who are forced to work with them and the rest of the people (sorry) less smart they made slaves. Although Bermuda is actually a mystery Segitiga this "owned" the United States, we do not apalah consecutive discuss its. Actual place of this kind there are in other places, also in the United States, which is in a lake called Ontario, and even more "chilling" Segitiga of Bermuda. Of different conclusions, compass needle aircraft and equipment that will always get lost and disruption as they do not see the water and from this gejalan concluded, on the sea floor there certainly there is a magnetic field is very strong, able to disrupt a compass or the ship is interesting to seabed in the.
Not enough if I decipher all the events, and is also not menjurus on the settlement. But the events in the form of magical Segitiga enjoy oneself and this can be possible theories about the many Segitiga Bermuda. May be in the air there is a kind of atmosphere in the form of interference "hole in the sky." To the hole that is the aircraft able to go without out. The mystery of "Hole in the sky" was formed a theory about the existence of such a relationship between the world with another dimension. hole in the sky that is considered a kind of means of transportation such as appear in the film Star Trek. Or the form of a hole in the sky UFO? People often connect us with the loss of aircraft UFO appearance. So, if the loss is because they are rapt by UFO? Even the results only get questions without answers.
There are places in Bermuda Segitiga called the Tongue of the Ocean or the "Ocean Lilah." Ocean have a tongue down the sea cliff (canyon) Bahamas. There are several events in an accident there. Not that many have not known about Segitiga Bermuda, so the mystery of the Bermuda Segitiga with other mysteries. For example, the mystery of the Sea Dragon has ever appeared in Tanjung Ann, Massachussets U.S., in August 1917. Possible sea dragon is a lot of victims that request? Or Cromwell currents in the Pacific Ocean that causes the ocean waves there or hurricanes, earthquakes in the bottom of the oceans? There are no people who know.
Bermuda Triangle really interesting, and frightening. Perhaps the Caribbean is a place that saves a lot of curiosity-curiosity, such as light-light that is not originally clear, shadow-frightening shadows, the exit sign in the sea surface, but the shape is not clear from the larger whales. Shaped like a giant jellyfish with color and keputihan been seen by two people (not so halutination).
"Jellyfish giant" as it is able to disrupt the compass needle and absorb physical energy. Perhaps the "giant jellyfish" is not a beast, but a UFO base can go out from the sea. Bizarre another island near Puerto Rico, it appears a giant water spout that formed a mushroom brush or flowers. Sea in a place that has the depth to 10 km. This incident was seen by Boeing 707 crew on 11 April 1963. According to them it must have a diameter selebar 900-1800 meters with a height half.
See the reality-and the fact that there is evidence that it is loaded, timbullah various forms of theory that may be different from one another. Theories that have been raised to open the mysterious disappearance of ships, among others: There is a natural hazard / earthquake that can be interesting ship tersedot. The existence of the various currents that come together in the area of Bermuda Segitiga that, so it may flow down suddenly changed to the surface and cause a vortex. Found Blue Hole, but it is still doubtful, because the large ships such as tankers / ships parent may not be able disedot by the Blue Hole.
There was a quake that caused a fracture of the land and water form a vortex and suck up to them. There is a waterspout vortex or wind can cause the destruction of an aircraft because dihempaskan. Other reviews, in the South Pole there is a large hole that connects the outside world with the other (whether true or not). There have been people named Admiral Bryd, view from the ship to fly to Jakarta in the south polar land turn to the lake that is not frozen and wild animals like Bison and see the human-like primordial man. Bryd as scientists reported pristiwa it, but nothing mempercayainya. Have you heard the story of alien abduction experienced by Herbert Schirmer have a base in the offshore Florida (Segitiga Bermuda) and one of earth's poles? Perhaps there is a UFO base that is aimed less good? Kitapun have the same Segitiga such as Bermuda, the mystery story Nyai Roro Kidul, unfortunately it was never a scientific investigation. Are there UFO base there? South Sea trusted person as a residence jinn.
Adam Bridge
 Adam Bridge, or the Rama Bridge is one of the "Mysterious Places in the World's." Mysterious ancient bridge along the 18 miles (30 km) which connects between Manand Island (Sri Lanka) and Pamban Island (India) has estimated that this was 1000. 000 more years!
Adam Bridge, or the Rama Bridge is one of the "Mysterious Places in the World's." Mysterious ancient bridge along the 18 miles (30 km) which connects between Manand Island (Sri Lanka) and Pamban Island (India) has estimated that this was 1000. 000 more years!
The image of Rama's Brige own very easily visible from the top surface of the sea water because of the location that is not too deep, that is only as deep stagnant approximately 1.2 meters (if the sea water are retroactive). Status page from the bridge is still a mystery to this day, according to the interpretation of experts, may be estimated Rama Bridge is very closely related with the famous Indian epic, Ramayana. Srilankan Archeology Department has issued a statment age of Rama Bridge may range between 1,000,000 to 2,000,000 years old, but whether this bridge actually form naturally, or is a human Mahakarya that they can not tell.
SUDeraniyagala, Director General of Archeology of Sri Lanka is also the author of the book "Early Man and the Rise of Civilization in Sri Lanka: the Archaeological Evidence" to say that human civilization has emerged in markets around Gunung Himalaya 2,000,000 years ago, although according to the historian of civilization the earliest didaratan India is a nation of Ca, it is not a guarantee that there is a more ancient civilization from them before. The degree estimate that the bridge may be built upon this ancient land separated by Sri Lanka India millions of years ago.
 In the epic Ramayana, the bridge was built by the troops under the control of human primates Rama.Maksud's own development is as a place to penyebrangan Affairs Alengka mission to rescue Shinta Dewi, which at that time are Dewi Sinta penculikannya in the Kingdom by King Alengka, namely Rahwana. Epic Ramayana, the Hindu calendar should be on the Tredha Yuga (according to the evolution of Hindu disc / disc epic about Hinduism is divided on the Sathya (1,728,000 years), Tredha (1,296,000 years), Dwapara (8.64.000 years) and Kali (4.32.000 years). Phase current according to their calendar is Kali.so,according to the epic, the age of Rama's Bridge around 1,700,000 years.
In the epic Ramayana, the bridge was built by the troops under the control of human primates Rama.Maksud's own development is as a place to penyebrangan Affairs Alengka mission to rescue Shinta Dewi, which at that time are Dewi Sinta penculikannya in the Kingdom by King Alengka, namely Rahwana. Epic Ramayana, the Hindu calendar should be on the Tredha Yuga (according to the evolution of Hindu disc / disc epic about Hinduism is divided on the Sathya (1,728,000 years), Tredha (1,296,000 years), Dwapara (8.64.000 years) and Kali (4.32.000 years). Phase current according to their calendar is Kali.so,according to the epic, the age of Rama's Bridge around 1,700,000 years.
How to Protect Your Computer From Spyware Computer
If you own a computer, you should be aware of the dangers posed by people secretively installing spyware computer software on your computer. Are you familiar with them? This form of privacy violation is not only a crime in most places, but it has become one of the leading security issues with computers and can pose a big risk to your personal information.
Unbeknownst to many people, spyware computer software is software that can be installed onto a computer by an outside user and used to collect personal and other valuable information stored. It also enables those who install it to partially control the interaction you have with your computer. This means that among other things like redirection while doing online searches, payments you make online can also be diverted to other places. That means that when you shop online, pay bills or transfer money in any way, unless you have protection against it you are at risk of having this money diverted, as well as the information you use to pay for it collected by an outside source.
To avoid this you should make sure you use security measures like firewalls, which block access to websites known to install spyware. Another security measure against spyware computer software is making sure that you only download from sites that are trusted and secure. One of the leading ways that spyware gets into your computer, is when it is attached to other programs that you can download off the Internet. Beware of downloads and unsecured, un-reputable sources! They may offer you free downloads, and even sometimes downloads you pay for that have spyware computer software attached to them! Of course, the best way to prevent spyware is to purchase a trusted anti spyware software program. These are designed for the express purpose of stopping spyware and there are a few to choose from that get the job done.
Because of the threat that this poses many countries have passed laws against the use of spyware computer software. However, it still happens. That is why a market that offers anti spyware security has also become popular. You can go online or ask anyone who knows about computer security and they will probably be able to rattle off to you some of the leading names in anti spyware software. Nonetheless, the best way to decide which is best for your needs is to do your own research. In addition, the best way to start is to be informed on the specifics of spyware computer software.
For those not too familiar with computer "lingo", trying to understand things like the dangers of spyware computer software might seem like a complicated task. However, just familiarizing yourself with what it is on a basic level can help you to understand how the protections against it work, and what you can do to protect yourself against it. Although this may seem like hours of work, it may be the thing that best protects you against identity theft, fraud, and theft of your money and personal information.
Some of the things you may wish to know more about is how spyware gets into your computer, what kinds of threats it poses, how to recognize signs that your computer has been infected with it and how to resolve and save your privacy if you have been infected with spyware computer software. Some of this information has been touched upon briefly, but there is much more out there available to you, so be proactive.
Spyware can also be installed into your computer at work, and most often this is also a place that holds information you don't want to share with strangers, especially those that are intentionally trying to steal it from you. Make sure you ask your employer or company what kind of protection they have in their computer systems to protect against spyware.
If you follow these suggestions, you can do a great deal in avoiding the damage and loss that can be incurred when your computer at home, or at work, becomes infected with spyware computer software. Save yourself the worry, and take action today. You will not regret it!
Be sure to use all of these considerations so that it will be easier to protect the computer and that the best and safest software can be downloaded onto the computer.

